VLAN (Virtual Local Area Network) tagging is a technique used in computer networking to allow multiple VLANs to coexist on the same physical network infrastructure, such as Ethernet. VLAN tagging involves adding an additional header to Ethernet frames to identify which VLAN the frame belongs to. This allows network switches to differentiate between traffic from different VLANs and appropriately forward the frames to their destination VLANs.
Sharing knowledge and experiences in networking, security, certifications (CCNA to CCIE), scripting, testing, virtualization, Kubernetes, and the cloud.
Friday, December 31, 2021
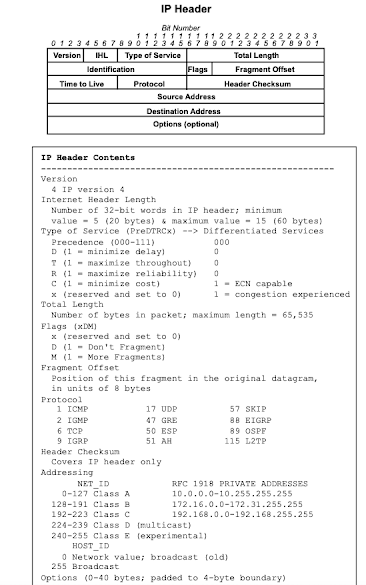
All Headers - TCP, IP, UDP, ARP, DNS, ICMP, Ethernet, IPSec, Vlan tagging
VLAN (Virtual Local Area Network) tagging is a technique used in computer networking to allow multiple VLANs to coexist on the same physical network infrastructure, such as Ethernet. VLAN tagging involves adding an additional header to Ethernet frames to identify which VLAN the frame belongs to. This allows network switches to differentiate between traffic from different VLANs and appropriately forward the frames to their destination VLANs.
Troubleshoot CLI's - ESX, NSX, NSX-Intelligence, Edge, FW, IDS/IPS
==========
nsx-mgr-1> get managers
nsx-mgr-1> get management-cluster status
nsx-mgr-1> get cluster status
nsx-mgr-1> get nodes
nsx-mgr-1> get interfaces
nsx-mgr-1> get transport-nodes status
nsx-mgr-1> get configuration
nsx-mgr-1> get cluster config
nsx-mgr-1> get firewall summary
nsx-mgr-1> get firewall published-entity
nsx-mgr-1> get firewall status
nsx-mgr-1> get logical-routers
nsx-mgr-1> get logical-switches
nsx-mgr-1> get service manager
nsx-mgr-1> get log-file syslog follow
nsx-mgr-1> get logging-servers
root@nsx-mgr-1:~# tail -f ./var/log/proton/nsxapi.log
root@nsx-mgr-1:~# tail -f /var/log/policy/policy.log ## policy mgr logs
nsx-mgr-1> set service manager logging-level debug
nsx-mgr-1> get logical-switch <id> arp-table
===================
> get intelligence flow config
Displays current PACE flow configuration
> get intelligence flow stats
Displays flow export statistics
> get intelligence flow stats ack
Displays flow export acknowledgement stats
======
List the VIBs loaded on ESXi
[root@prom-05056b17085:~] esxcli software vib list | grep -e nsx -e vsip
Host to mgr communication
[root@prom-05056b17085:~] esxcli network ip connection list | grep 1235
[root@prom-05056b17085:~] esxcli network nic list
[root@prom-05056b17085:~] esxcli network firewall ruleset set -r syslog -e true
[root@prom-05056b17085:~] esxcfg-nics -l
[root@prom-05056b17085:~] tail -f /var/log/dfwpktlogs.log
===============
[root@prom-05056b17085:~] tail -f /var/log/dfwpktlogs.log
[root@prom-05056b17085:~] summarize-dvfilter ## get the VM interface ID
[root@prom-05056b17085:~] vsipioctl getrules -f nic-6389857-eth2-vmware-sfw.2
[root@prom-05056b17085:~] cat /var/log/dfwpktlogs.log
[root@prom-05056b17085:~] nsxcli
prom-05056b17085.system.test> get logical-switches
prom-05056b17085.system.test> get firewall vifs
prom-05056b17085.system.test> get firewall rule-stats
prom-05056b17085.system.test> get firewall status
prom-05056b17085.system.test> get firewall <vifuuid> ruleset rules
prom-05056b17085.system.test> get firewall <vifuuid> addrsets
prom-05056b17085.system.test> get logical-router 51515dfa-b15a-45d6-9d60-90e4c40023e1 interfaces
prom-05056b17085.system.test> get logical-router 51515dfa-b15a-45d6-9d60-90e4c40023e1 interface 85d532cc-2627-4ae0-8ee6-e7ba38f67572
prom-05056b17085.system.test> get host-switch PROD-Overlay-NVDS tunnels
===
[root@blrkv-hs1-b0606:~] esxcli network ip interface ipv4 get
[root@blrkv-hs1-b0606:~] esxcli vm process list
[root@blrkv-hs1-b0606:~] esxcli storage vmfs extent list
=========
edge> get service ssh
edge> get configuration
edge> get interfaces
edge> get managers
edge> get host-switches
edge> get tunnel-ports
edge> get vteps
edge> get logical-routers
edge> get logical-switches
edge> get firewall interfaces
edge> get firewall <interfaceid> ruleset
edge> get firewall <interfaceid> ruleset rules
edge> get dhcp ip-pools
edge> get dhcp leases
===============
Intel> get service
Intel> get version
Intel> get services
get log-file syslog | find pace-monitor
Intel>restart service service-name
root@Intel:~# cat /var/log/pace/token-registration.log
root@Intel:~# cat /var/log/pace/pace-server.log
root@Intel:~# journalctl -u pace-monitor -n 60 --no-pager
Intel> get service druid
====
root@systest-runner:~[1156]# curl -k -u username:password https://<nsx-ip>/api/v1/firewall/status
root@systest-runner:~[1158]# curl -k -u username:password https://<nsx-ip>/api/v1/firewall/sections/<id>/rules
root@systest-runner:~[1168]# curl -I -k -u admin:VMware1VMware! https://<nsx-ip>/policy/api/v1/infra/realized-state/realized-entities
=================
root@ubuntu-1804:~# nmap -T4 -Pn -A -v <server-ip>
Starting Nmap 7.60 ( https://nmap.org ) at 2021-12-07 11:01 UTC
NSE: Loaded 146 scripts for scanning.
-T<0-5>: Set timing template (higher is faster)
-A: Enable OS detection, version detection, script scanning, and traceroute
-v: Increase verbosity level (use -vv or more for greater effect)
-V: Print version number
-Pn: Treat all hosts as online -- skip host discovery
===========
[root@prom-05056b17085:~] nsxcli -c get ids engine stats
[root@prom-05056b17085:~] nsxcli -c get ids events stats
================
edge(tier1_sr[1])> get interfaces
edge(tier1_sr[1])> get interfaces stats
edge> start capture interface <id>
edge> start capture interface <id>
root@ubuntu-1804:~# nmap --script http-vuln-cve2014-3704 --script-args http-vuln-cve2014-3704.uri=“/drupal”,http-vuln-cve2014-3704.cleanup=false <server-ip> --disable-arp-ping
[root@blrkv-hs1-b0606:~] cd /var/log/nsx-idps
[root@blrkv-hs1-b0606:/var/log/nsx-idps] summarize-dvfilter
To confirm that IDS is enabled on this host, run the command get ids status
On ESX -> nsxcli
[root@prom-05056b1c8f2:/var/log/nsx-idps] vsipioctl getflows -f <nic>
[root@prom-05056b17085:/var/log/nsx-idps] vsipioctl getfwconfig -f <nic>
Monday, December 27, 2021
DevOps Basics
• Linux administration
• Scripting (Python or Go)
• Networking fundamentals
• Git version control
2. Embrace Containers and Cloud:
• Docker containerization
• Cloud platforms (AWS, GCP, Azure)
3. Build Robust Delivery Pipelines:
• Advanced CI/CD implementation
• Kubernetes for container orchestration
4. Focus on Observability:
• Monitoring and logging tools
• Infrastructure as Code (Terraform)
5. Ensure Production Readiness:
• Security and compliance automation
• Service mesh implementation (e.g., Istio)
• Chaos engineering for resilience testing
6. Gain Real-World Experience:
• Personal projects
• Open source contributions
• Entry-level DevOps roles
7. Consider Certifications:
• AWS Certified DevOps Engineer
• Similar respected credentials
Git is a protocol or the version control system that helps us track and merge changes.
And Github is the GIT server that host remote repositories.
Webserver introduction:
Say we have website, it’s an e-commerce application. It is hosted on a webserver. So when a user opens a browser and types in the address to the server, a request is sent to the server hosting the application.
On receiving the request, the server sends back its response which is the web page along with the data about a list of products available on the site. And that’s what the user sees on the page. The machine running the program is the web server and the browser is the client. The client sends a request to the server and the server returns a response. So there are two sets of code in work here.
A set of code that runs on the server side that is actually hosting the web server and that’s the code that’s listening for connection from users and querying databases, etc. So, this is called the server-side code or the backend code.
This is usually written in programming languages like Java, Python or NodeJS. And the response sent back by the server could be another set of code that runs on the client-side that is used to display webpages and information within the pages. These are called client-side code or also referred to as front-end code. These are usually in the form of HTML, CSS, and JavaScript.They run on the client-side in the user’s browsers. Users can even see that code inside their browser using the browser developer tools. So both these sets of code are developed together as part of the same application.
Say you have server-side code written in Java that uses a Spring Boot web framework.
Now you have developed the code of your web application, but how do you serve it? How do you run it so this code listens on a port and responds back to the users?
For some of these frameworks like Python, for example, flask, for instance, provides a way to run the application natively but it is not recommended for hosting the application in a production environment. Thats where a web server comes in so while a web framework is what helps you develop application code and web server is what hosts this application.
So you basically take all your code that you have developed and put it on a web server. Note that the code need not be in the original format, it could be in case of Python or NodeJS based application, but in case of JAVA, it is usually packaged. So Apache Tomcat, GlassFish, Nginx, GUnicorn, uWSGI are examples of servers that can host web applications. The webservers run one or more processes that listen on a particular port for requests and performs the required operations and responds back to the users. Once done, for example, Tomcat listens on port 8080 by default, whereas Nginx listens on port 80, and Gunicorn listens on port 8000 by default. And off-course these port can be change as per our wish. Also, web servers can host multiple applications at the same time. So, they can redirect requests based on the URL or hostname or a path to different applications.
Websites can be broadly classified into two types:
A website that only uses HTML pages, some CSS styling, and images such as a website that shows a list of pictures as an image gallery could be classified as a static website because it only uses static content. That is content that does not change like HTML files and CSS files. There is no real interaction with the server after the content is served. However, an e-commerce website that lists products and provides the ability for users to add a cart and make purchases are called dynamic websites. They often have a back-end and some logic running for processing payments, shipping orders, getting a list of products and purchases, etc. So dynamic websites usually require both static and dynamic content. That is static content as HTML pages and images are used to show the webpage, but at the same time, information about products are retrieved form the database before displaying them on the web page, So, web pages are likely to be displayed differently based on the data in the database. And that’s why they are called dynamic websites so they have code and databases in the backend.
There are different web server technologies that serve different purposes. The Apache HTTP web server and NGinx are good example of static web servers that serve static content. Whereas the Apache Tomcat, uWSGI, Gunicorn are good examples of dynamic web servers or application servers.
Static web servers are usually referred to as web servers, and servers that host dynamic web sites are referred to as application servers.
Apache Web server:
The Apache web server is an open-source HTTP server developed and maintained by the Apache software foundation. It is a web server, usually used to serve web content like HTML, CSS, and JavaScript files.
It also used in conjunction with an application server that acts as a back-end for running business logic, such as Apache Tomcat server.
Install Apache web server:
yum install httpd
service httpd start
service httpd status
If you have firewall configured on your system, then make sure to add a rule to allow HTTP traffic.
View logs:
Every server has a path where it stores the logs. To view log files
cat /var/log/httpd/error_log
cat /var/log/httpd/access_log
The access logs are update whenever a user accesses the website, and the error logs are updated whenever there is an error. Also every server has a configuration file, where you configure the different parameters that govern
How the server operates, such as what port it listens on and where the static content is stored and any SSL or HTTPS configurations, where logs are stored etc. In case of apache web server, it is at, /etc/httpd/conf/httpd.conf path.
The DocumentRoot defines the location where static content is stored. So move all the static contents of your website to this directory. Another configuration is the server name for this you must have a DNS entry configured in your networks DNS server to point that host to the IP address of your system.
A single apache server can host multiple websites. To do that, the files and configuration of each website is configured as a virtual host within the apache configuration file. So, a virtual host is a logical division of the Apache web server.
Each virtual host can be configured with its own server name and document root. Each virtual host configuration file can also be moved to separate configuration file.
Apache Tomcat:
The Apache Tomcat server provides a web server environment where we can host Java-based web applications. So as a prerequisite you must have java installed.
By default apache web server runs on port 80 and Apache Tomcat on port 8080. The apache Tomcat server is a web server capable of hosting multiple Java web applications. Once you extract the package under bin you can find .bat files for windows and .sh for linux. Out of these startup.sh and shutdown.sh scripts are used to start and stop the Tomcat server. Under conf directory we have multiple conf files where we configure what port to listen and how to direct the traffic between the different web apps, etc. The server.xml file has entry for connector. The connector is the endpoint at which the requests are received. So it’s set to 8080 and that’s the default port that Tomcat listens on, and the port number can be changed if required. Any change will require a restart of Tomcat service. The web dot.xml file is used to deploy and configure web applications. The logs directory is where the logs are stored. And the web apps directory is where web applications hosted by Tomcat server are located and this is where you should place your application that you want apache to serve.
Database basics:
Databases are a key component of system Design
Operations engineers deploy and manage databases
Applications read and write to these databases
Mostly databases are categorised as SQL and non-SQL based. MySQL and PostgreSQL are SQL based and MongoDB, Cassandra are example of Non SQL DB.
SQL or relational DB store data in the form of rows and columns. Adding additional entry will affect complete data.
No SQL databases store information in the form of documents or pages, These files can be in any format or structure and changes to one file does not affect the others.
In summary in SQL each person data is represented in a row but in No SQL each person gets their own document. Together all rows in a SQL database form a table. In a no SQL database, all documents together form a collection.
We typically use SQL queries to query and filter data from a SQL database.
Famous websites like fb, Goggle and Youtube use MySQl as their database.
Log location is /var/log/mysqld.log
The default port that MySQL listens on is 3306
MongoDB is an Open source, NoSQL, scalable and high performance also known as document database as it stores data in JSON like document format. Multiple documents together form a collection. Multiple collections together form a database and you can have multiple such databases with a single MongoDB server.
Logs are stored at path /var/log/mongodb/mongod.log
Default port that MongoDB listens on is 27017
These setting can be changes at configuration file located at /etc/mangod.conf
DevOps is a set of practices, principles, and cultural philosophies that aim to improve collaboration, communication, and integration between software development (Dev) and IT operations (Ops) teams. The primary goal of DevOps is to streamline the software delivery process, accelerate deployment cycles, and improve the quality and reliability of software applications. DevOps emphasizes automation, continuous integration (CI), continuous delivery (CD), and close collaboration between development, operations, and other stakeholders throughout the software development lifecycle (SDLC).
Key aspects of DevOps include:
1. **Culture and Collaboration**: DevOps promotes a culture of collaboration, transparency, and shared responsibility across development, operations, quality assurance (QA), and other teams involved in software delivery. It encourages breaking down silos between teams, fostering open communication, and promoting a "fail-fast, learn-fast" mentality.
2. **Automation**: DevOps advocates for the automation of repetitive tasks, such as code builds, testing, deployment, and infrastructure provisioning. Automation helps reduce manual errors, improve efficiency, and accelerate the software delivery process.
3. **Continuous Integration (CI)**: CI is a practice in DevOps where developers frequently integrate their code changes into a shared repository (e.g., version control system) multiple times a day. Each integration triggers automated builds and tests to ensure that the codebase remains stable and functional.
4. **Continuous Delivery (CD)**: CD extends CI by automating the release process to ensure that software can be deployed to production environments quickly, reliably, and frequently. CD pipelines automate deployment, testing, and validation tasks, enabling organizations to release new features and updates to end-users with minimal manual intervention.
5. **Infrastructure as Code (IaC)**: IaC is a DevOps practice where infrastructure resources, such as servers, networks, and databases, are defined and managed using code and configuration files. IaC enables the automation of infrastructure provisioning, configuration, and management, making it easier to scale, replicate, and maintain infrastructure environments.
6. **Monitoring and Feedback**: DevOps emphasizes the importance of monitoring application performance, infrastructure health, and user feedback. Continuous monitoring helps identify issues, track performance metrics, and gather insights for continuous improvement and optimization.
7. **Security and Compliance**: DevOps integrates security and compliance practices into the software delivery pipeline from the early stages of development. DevSecOps extends DevOps principles to include security considerations throughout the SDLC, ensuring that security is built into the software from the outset.
Overall, DevOps is a holistic approach to software development and operations that fosters agility, collaboration, and innovation, enabling organizations to deliver high-quality software products and services more efficiently and reliably in today's fast-paced digital economy.